Introduction
Data security is a critical consideration in any business intelligence (BI) solution, and Power BI is no exception. As developers, we have a responsibility to ensure that the data we collect, analyze, and visualize is secure from unauthorized access, breaches, and other security threats. In this blog, we will discuss some of the best practices for data security in Power BI that can help us keep our data safe.
1.Use Azure Active Directory for Authentication
Azure Active Directory (AAD) is the recommended option for authentication in Power BI. AAD enables us to control access to our data by setting up permissions for users, groups, and applications. With AAD, we can authenticate users using multi-factor authentication, enforce password policies, and monitor user activity. To set up Single Sign-On (SSO) with AAD in Power BI, we can follow the steps shown in the image below:
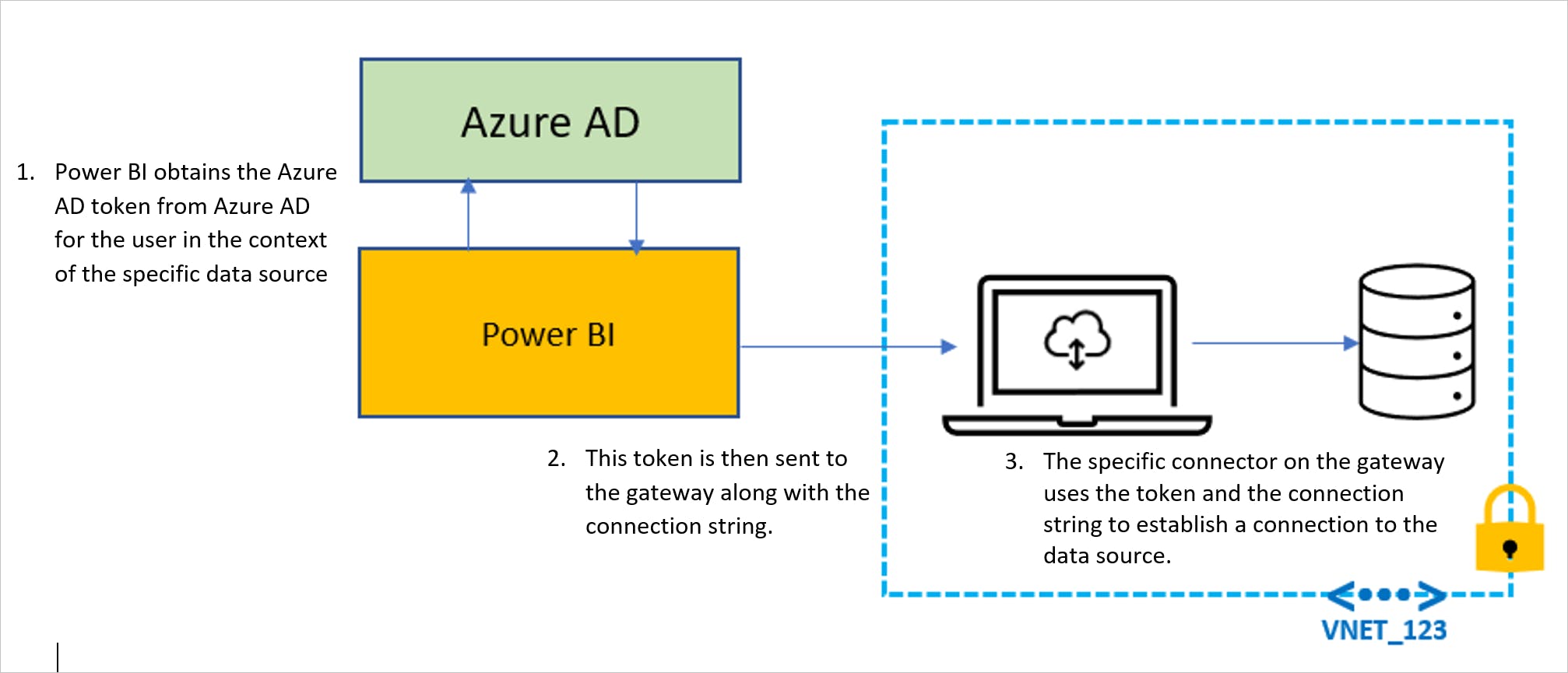
Image Source: Microsoft Power BI Documentation
Using AAD, we can integrate with other Microsoft services, such as Office 365 and Dynamics 365, to provide a seamless authentication experience across our applications. By using AAD, we can simplify user management, reduce the risk of data breaches, and comply with industry standards such as GDPR and HIPAA.
2.Implement Row-level Security
Row-level security (RLS) is a powerful feature in Power BI that enables us to restrict access to specific rows of data based on user roles or attributes. RLS ensures that users see only the data that they are authorized to see, and it prevents unauthorized access to sensitive data.
For example, we can create a role that allows users to see only the data that pertains to their department or location. We can also set up dynamic RLS that changes based on user attributes such as job title or tenure.
RLS can be implemented using Power BI Desktop or by using a data model that supports RLS, such as SQL Server Analysis Services (SSAS) or Azure Analysis Services. By using RLS, we can ensure that our data is secure and compliant with industry regulations.
3.Use Power BI Encryption
Power BI uses several encryption mechanisms to protect data at rest and in transit. Data at rest is encrypted using 256-bit Advanced Encryption Standard (AES), which is considered one of the strongest encryption algorithms. Data in transit is encrypted using Secure Sockets Layer (SSL) or Transport Layer Security (TLS), depending on the data source. We can also enable Azure Rights Management (Azure RMS) for additional data protection.
Power BI also supports encryption of data sources, such as SQL Server, Azure SQL Database, and SharePoint Online. By using encryption, we can protect our data from unauthorized access and ensure that it is secure both in transit and at rest.
4.Enable Auditing and Monitoring
Auditing and monitoring are critical for detecting and preventing data breaches. Power BI provides auditing and monitoring capabilities that allow us to track user activity, monitor data access, and detect security threats.
We can use Power BI auditing to monitor user activity such as login attempts, report access, and data export. We can also use Azure Monitor to monitor data access and set up alerts for suspicious activity. By enabling auditing and monitoring, we can detect security threats early and take action to prevent data breaches.
5.Control Data Refresh
Data refresh is a critical aspect of data security because it determines when and how data is updated in Power BI. We can control data refresh by setting up a refresh schedule, enabling incremental refresh, and restricting data refresh to specific users or groups.
By setting up a refresh schedule, we can ensure that data is updated only when it is necessary and that it does not put unnecessary strain on our data sources. By enabling incremental refresh, we can reduce the amount of data that needs to be refreshed, thereby improving performance and reducing the risk of data breaches. By restricting data refresh to specific users or groups, we can ensure that only authorized users can refresh data and prevent unauthorized access.
6.Use Power BI Gateway
Power BI Gateway is a data transfer tool that enables us to connect on-premises data sources to Power BI. Gateway uses several security mechanisms, such as SSL/TLS encryption and OAuth 2.0 authentication, to ensure that data transfer is secure and compliant with industry standards.
By using Power BI Gateway, we can ensure that our data sources are secure and that data transfer between our on-premises data sources and Power BI is encrypted and authenticated.
7. Enable Data Loss Prevention (DLP)
Data Loss Prevention (DLP) is a feature in Power BI that enables us to prevent sensitive data from being shared or leaked. DLP allows us to define policies that restrict data sharing based on the sensitivity of the data.
For example, we can set up a policy that prevents users from exporting data to Excel or other applications or restricts data sharing to specific users or groups. By using DLP, we can prevent data breaches and ensure that our sensitive data is secure.
Conclusion
Data security is a critical consideration in any BI solution, and Power BI provides several features and mechanisms that can help us keep our data secure. By following the best practices outlined in this blog, we can ensure that our data is secure from unauthorized access, breaches, and other security threats. As developers, it is our responsibility to ensure that our solutions are secure and compliant with industry standards. By implementing these best practices, we can provide our users with a secure and reliable BI solution that meets their needs.